-
IF you assign a single STATIC IP address behind your network, you CAN NOT disable the firewall. This might be good if you have to have certain traffic come FROM an IP address, but don't want any inbound access to the device.
-
To disable the firewall, you will need to setup the device as a DHCP Client.
-
You will only be able to have 1 "Device" per Static IP when using DHCP.
-
With a FortiGate, it could be possible to have VDoms to get "multiple" devices, but dual WAN addresses are not supported for some reason. I have tried and tested as well as found other complaining of the same issue. I will dig up the reasons a very smart man has figured out shortly.
-
Once configured correctly, your Device will get a DHCP address from a PUBLIC block and not a private block, thus giving you a public IP on your firewall.
-
For network admins and network enthusiasts, this is a very confusing situation. But it is, what it is.
Here is how I accomplished this.
Recently I was tasked with bringing a ATT uVerse client online with a new SBS server. They needed site-to-site VPN's between the sites as well as public services forwarded to their SBS server for things like RWW, SMTP, OWA, RDP, etc...
We obtained a 5-block of Static IP addresses and off we went.
After talking to the first 3 "Level 2" technicians, I was confident that I was to statically assign an IP address to my FortiGate 50b WIFI's WAN1 IP, then I could set it up with Static IP's.
So I went ahead and did the obvious to setup a Static IP on my WAN1, configured Default Routes and Firewall policies. After logging on, I found that the www.ipchicken.com saw my static IP address and I thought I was set. Oh, how I was so wrong...
After returning, I tried to access the Public IP of the Firewall to configure some services, even though I had Ping and HTTPS forwarding configured, I was unable to do either. After doing a sniff of the WAN1 interface, I found that the traffic was not making it to the WAN1. Obvious... A firewall.
So I am making this quick guide so that you can save several hours. Here are VERY important details of how this has to work:
-
Pending you have previously been using the ATT modem as a router before trying to install the FortiGate UTM Firewall, you will need to connect to the IP of the uVerse router.
-
To find this, open a command prompt, and type 'ipconfig' The Gateway IP is your ATT uVerse Modem.
-
Open a web-browser and type in the IP of the gateway. In this instance it is 192.168.6.254.
-
Open Home Network and Advanced
-
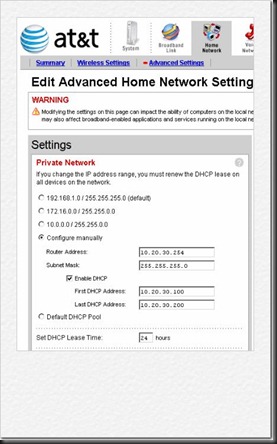
Configure a new IP and DHCP Pool on your ATT DSL Modem (2701HGV-B). Lets use 10.20.30.254/24 (255.255.255.0) with a DHCP Pool from (10.20.30.100 through 10.20.30.200), we'll only need 1 IP/device.
-
When you click "Save" you will loose connection to this device. That is fine, just disconnect all devices except the WAN1 for the firewall
-
IMPORTANT!!! Disconnect all devices from the ATT modem and only have your FortiGate WAN 1 Attached Only to the DSL/ATT Modem.
-
Connect to your FortiGate firewall and login. If you do not know how to do this, please visit my other blog Using a Console Cable to configure a Fortinet Appliance. Change the "Internal Interface" what ever it may be in your situation to a Static or Manual IP. We will reuse our previous 192.168.6.254/24 address, so that we do not have to change any static device on the Internal network. It is suggested that if the IP subnet is 192.168.0.* or 192.168.1.*, to change to a different address. It is possible to use any address below 255 on the following schemes. (10.*.*.*, 192.168.*.*, or 172.16.*.*).
-
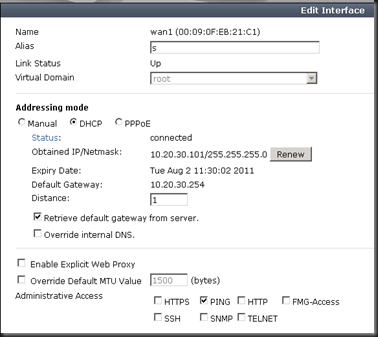
Configure the FortiGate WAN1 with a DHCP Address, you should get an address of 10.20.30.*, it will likely be 100, but not always.
-
Configure your Internal Interface with the old ATT Default Gateway (Or the Default Gateway of your choosing). In our instance it will be 192.168.6.254, please make sure to check Ping, SSH and HTPS, we might need these!
-
Configure a simple Internal-->WAN1 policy with NAT enabled.
-
Connect to the Fortigate Internal (Default Gateway) IP via https, using the IP we provided as the Internal IP. Login
-
Open another browser page to connect to the ATT uVerse modem/router via http://10.20.30.254
-
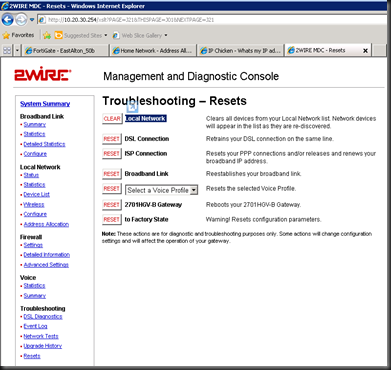
Clear the ATT Routers Machine Cache before starting by visiting the http://10.20.30.254/mdc
-
On the Left column, go to Resets and click the first Item "Reset Local Network". This should clear your device list under http://10.20.30.254 (Home Network)
-
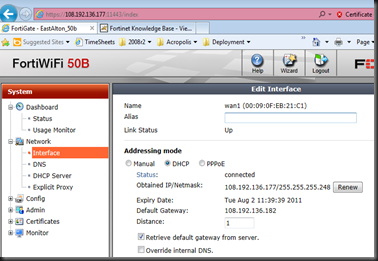
Go to the FortiGate Device https://192.168.6.254, Status-->Network-->Interface. Edit WAN1, and click "Renew" next to DHCP.
-
Go back to the ATT router and you should see the FortiGate device listed.
-
Click Broadband Link-->Advanced
-
On the left column, select "Routed Interface", Fill in the gateway provided by ATT as well as the subnet mask provided by them. Check the "Auto Open Firewall" checkbox. Click Save.
-
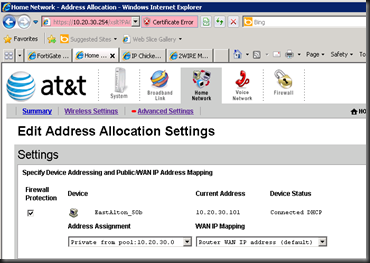
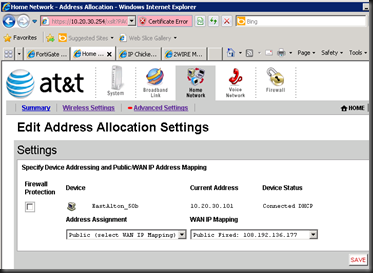
Click Home Network-->Advanced and then "Edit Address Allocation" on the right column.
-
Inside of here, we will assign the Public IP to the FortiGate. For us Network Administrators, this is a VERY strange way of doing things. Please hang in there, we are almost done.
-
Inside the "Edit Address Allocation" section, you should see your single device.
-
Click the Address Assignment and scroll up, on top of the scroll list, is a "Assign Public IP" option. Select this.
-
Click WAN IP Mapping on the right side. This should have a dropdown with your Public IP blocks. Choose any that you wish to use.
-
Uncheck the "Firewall" box to remove firewalling (finally).
-
Go back to the FortiGate Interface and click Renew under WAN1. You may have to do this a few times, but after a few times, you should now have a Static Public IP address.
Basically here are the steps:
Thank you to all who read and you are welcome to those that learned and may have saved a day of research and calling horrible ATT support.
Enjoy!

![A60BDD56C8241BA098A2AB5F35F61CE4A3AD03C6[1] A60BDD56C8241BA098A2AB5F35F61CE4A3AD03C6[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi42CVW4FZyqkgYSOsKMTHLyIX9pklcA_B2sSfA3zCLZ0eQBOfzvla2MIC9YSfzowcqZwPMLTKJNxvg86ifvHKrd9tgewrG3WWnNpTAlk4I49bLEN04J5iSUmj5Fz7RBk5YIrofISXpV1o/?imgmax=800)


Wow, that is crazy complicated to get a static IP address on your firewall. Luckily they only needed one IP address. It almost renders the other 4 "usable" addresses useless.
ReplyDeleteJust for clarification, this is not a problem or limitation on the Fortigate side of the equation. The problem is all on the 2Wire. Hopefully they release an updated firmware to make this process simpler and more flexible.
Is the "very smart man" you reference is Phil Karn: http://www.ka9q.net/Uverse/
Here is an interesting thread I found with a lot of comments from Phil Karn that seems very similar to the problems you report (although they are talking about a 3800 series modem) and even one where he mentions a possible solution (page 4) by blocking DHCP traffic between the modem and the firewall using a semi-transparent bridge:
http://www.dslreports.com/forum/r22423850-Using-a-3rd-party-VDSL-modem~start=60
Maybe since the FortiGate supports transparent bridge mode you could do something along those lines.
As you said, most of this applies to any firewall, steps for the firewall may be different screen to screen but the idea still applies.
ReplyDeleteGreat work on finding Phil.. Phil, if you ever read this, you made my eyes cross but a great write up that technically made me understand what I was up against.
Otherwise, enjoy the tips, hope it helps someone out there!
I am installing a FortiGate 50B with Comcast ISP. The network that is in place is static; it's a small network and has some hardware that works better when the address is locked. The post that you wrote has given me some insight on how I can keep from reconfiguring every node for DHCP. Thanks!
ReplyDeleteSo what happens when the 2701HGV-B doesn't have the "mdc" pages? :( I hate these devices.
ReplyDeleteRecently, a hacker is keep trying and guessing Fortigate 60B admin/root account. The Fortigate router is behind and bridged with the AT&T 2wire router. I did shutdown the AT&T 2wire router and let it getting a new ISP IP, but the hacker found my Fortigate again withing several hours. I also did the blocking IP on Fortigate by using the Virtual IP with NAT Virtual Group. The hacker keeps changing IP. The blocking IP seems not the permanent solution. Any idea how to prevent the situation from the hacker? Is It possible to hide the Fortigate logon GUI from the hacker/public?
ReplyDeletecharlih... Just to better understand, you want to be able to manage the firewall from anywhere, but block just that 1 IP at a time? Do you have an idea where you might be coming from subnet wise? Do you have a "jump off" point that has static IP's? The attacker isn't a person, it's likely an automated tool seeing your HTTPS and SSH ports open. I do have some tricks, I might just spend some time sharing how I do it.
ReplyDeleteCheck out my new blog entry to help understand a way to secure this down a bit. Enjoy!
ReplyDeletehttp://fortiblazin.blogspot.com/2012/07/securing-down-your-fortigate-utm.html