Securing it for a Static IP
If you have a Static IP or group of Static IP’s that you use to connect remotely to your Fortinet device, there is an easy way to map external services, secure it down to a group of subnets and allow only a few IP’s to remotely manage the firewall from the Internet. There are other ways, this is my favorite with the most amount of control and logging available for the remote connections. Let’s get started.
Scenario (My Setup)
- WAN IP = Dynamic (wan)
- LAN IP = 10.11.3.254 (InternalSwitch)
- Internal Management Port (HTTPS) = 443
- Internal Management Port (SSH) = 22
- Trusted External Subnets =
- 12.166.20.0/23
- utm.doesntexist.com (DynDNS)
Let’s get started with a Dynamic or Static IP
- Log into firewall
-
Create a new VIP for HTTPS Access

| config firewall vip | Enter into VIP |
| edit External_HTTPS_T11443_w1 | Name 1st VIP (I uses _w1 because you could create multiple for multiple WAN connections) |
| set extintf wan | Set External Interface |
| set mappedip 10.11.3.254 | Set Internal IP |
| set portforward en | Enable PAT |
| set extport 11443 | This is your External Port to Access GUI (I suggest not using 443) |
| set mappedport 443 | This is the Internal Mgmt Port (443 is default) |
| next | Next to start SSH entry, end to not setup ssh |
-
Create a new VIP for SSH Access
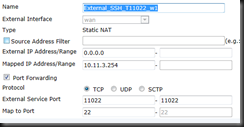
| edit External_SSH_T11022_w1 | Name this VIP, using _w1 to separate multiple WAN connections |
| set extintf wan | Set External Interface |
| set mappedip 10.11.3.254 | Set Internal IP |
| set portforward en | Enable PAT |
| set extport 11022 | This is your External Port to Access GUI (I suggest not using 22) |
| set mappedport 22 | This is the Internal Mgmt Port (22 is default) |
| end | end to save |

| config firewall vipgrp | Enter VIP Group Entry |
| edit ExternalManagement_w1 | Create a group for the External Management using _w1 to define the one for WAN1 |
| set interface wan | Set the Group’s interface (wan) in this scenario |
| set member “External_HTTPS_11443_w1” “External_SSH_T11022_w1” | Add the two members to the group |
-
Create address object for trusted IP

| config firewall address | Enter Address Creation |
| edit “TrustedSubnet_1” | Call this what you want, but you are creating a name for this trusted IP |
| set subnet 12.166.20.0/23 | Add the trusted subnet |
| next or end | Next or end to create more |
-
Create address object for trusted FQDN

| config firewall address | Enter Address Creation |
| edit “Trusted_FQDN_1” | Call this what you want, this is a trusted FQDN example |
| set type fqdn | Setup a type FQDN |
| set fqdn “utm.doesntexist.com” | Add your trusted FQDN |
-
Create address group object
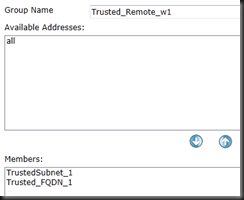
| config firewall addrgrp | Enter Address Group Creation |
| edit “Trusted_Remote_w1” | Create a group name for Trusted addresses on w1 |
| set member “TrustedSubnet_1” “Trusted_FQDN_1” | Add members to the Group |
| end | End to save |
-
Create new ExternalAdmin account

| config system admin | Enter Address Group Creation |
| edit ExternalAdmin | Create your ExternalAdmin Account |
| set accprofile super_admin | super_admin is a full rights admin, but I suggest creating a restricted user for External Access |
| set password SecurePassword | Change SecurePassword with a secure password |
| End | Save and create new Account |
-
Lockdown admin to local subnet only

| config system admin | Enter Address Group Creation |
| edit ExternalAdmin | Create your ExternalAdmin Account |
| set accprofile super_admin | super_admin is a full rights admin, but I suggest creating a restricted user for External Access |
| set password SecurePassword | Change SecurePassword with a secure password |
| End | Save and create new Account |
-
Create firewall policy
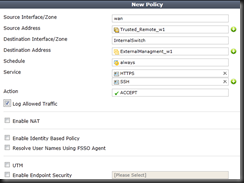
| config firewall policy | Enter Firewall Policy Creation |
| edit 0 | “edit 0” creates a new entry after the biggest number. |
| set srcintf wan | set the Source Interface (wan) in this instance, probably a port or wan1/2 for you |
| set dstintf InternalSwitch | set Destionation Interface (InternalSwitch). Likely a port or internal for you. |
| set srcaddr “Trusted_Remote_w1” | Set your Source Address. This is the group you created in previous steps |
| set dstaddr “ExternalManagement_w1” | Set your Destination Address. This is your VIP Group you created earlier |
| set action accept | Accept the traffic |
| set service “HTTPS” “SSH” | Set the two services you need. These are the “internal” services and not the external. If you management port is not standard you may need to create a service object for this. |
| set logtraffic enable | Enable logging for your sanity. |
| end | |
This will in effect do the following:
- Allow the default “admin” to only login from inside the network
- Create a new user for ExternalAdmin of the firewall
- Create 2 VIP’s to allow inbound mapping for alternative ports to the inside management ports
- Allow you to ping the firewall from anywhere
- Trust just a few IP/FQDN’s for remote management
- Log traffic accessing the VIP
- Apply inbound UTM if you wanted, not in this tutorial though
To use this you will want to either:
- To use web-management, use the IP of the External Interface to use
- https://externalIP:11443
- Use DynamicDNS to “find easier”
- Putty via externalIP:11022
- Login with ExternalAdmin and password
Hope this helps you create a secure access method to your firewall.
Enjoy!









No comments:
Post a Comment