It is possible that you’d want to allow access to an inbound “service” that needs authentication before you actually hit the service it’s destine for. Lets say you have a web-server on the inside of your firewall. It has semi-private data on it, that you can’t easily secure with the web-application. Maybe you have a situation where you just want the service to be protected with a pre-authentication so brute-force against the web-application won’t work correctly.
Here’s how:
-
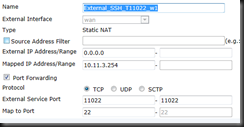
Create your VIP – If you don’t have one.
| config firewall vip | Enter into VIP |
| edit External_HTTPS_T11443_w1 | Name 1st VIP (I uses _w1 because you could create multiple for multiple WAN connections) |
| set extintf wan | Set External Interface |
| set mappedip 10.11.3.254 | Set Internal IP |
| set portforward en | Enable PAT |
| set extport 11443 | This is your External Port to Access GUI (I suggest not using 443) |
| set mappedport 443 | This is the Internal Mgmt Port (443 is default) |
| End | End |
-
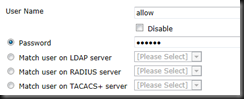
Create a local user account – You could use LDAP if you wanted, but not covered in this tutorial.
| config user local | Enter Local User Creation |
| edit allow | Enable the Account |
| set passwd SecurePassword | Set a Secure Password |
| end | End to save |
-
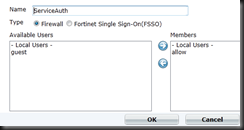
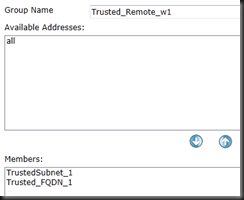
Create a group to use for policy
| config user group | Enter Group Creation |
| edit ServiceAuth | Name the group |
| set member “allow” | set the members, “allow” is the local account create previously |
-
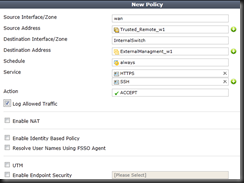
Config firewall policy - If you don’t have one.
| config firewall policy | Enter Firewall Policy Creation |
| edit 0 | “edit 0” creates a new entry after the biggest number. |
| set srcintf wan | set the Source Interface (wan) in this instance, probably a port or wan1/2 for you |
| set dstintf InternalSwitch | set Destination Interface (InternalSwitch). Likely a port or internal for you. |
| set srcaddr “all” | Set your Source Address. This is the group you created in previous steps |
| set dstaddr “External_HTTPS_T11443_w1” | Set your Destination Address. This is your VIP Group you created earlier |
| set action accept | Accept the traffic |
| set identity-based enable | Enable the ability to do Identity Based |
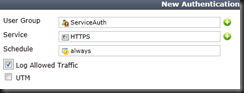
| edit 0 | Create next ID |
| set schedule always | Set schedule |
| set logtraffic enable | Set logging of traffic |
| set groups “ServiceAuth” | Set the group (Created earlier) |
| end | End the Identity policy |
| end | End the Firewall Policy Save |
How to use this new policy
- Regardless of service needed, port forwarded/authenticated or any other application using this policy, you must first authenticate to the firewall before using it.
- It is extremely important that you authenticate using HTTPS and not HTTP. Otherwise, your credentials pass in the clear.
- Ex. if protecting RDP, you have to first go to https://ExternalIP:3389 and login with the local/group that is allowed into the policy
- Once you authenticate, you can then RDP directly into the ExternalIP
- Once you authenticate, the authentication timer is started. It is possible you’d want to extend this
config user setting Enter the User Setting set auth-timeout 240 Set the timeout in minutes for 4 hours, 480 minutes is the max. end end and save